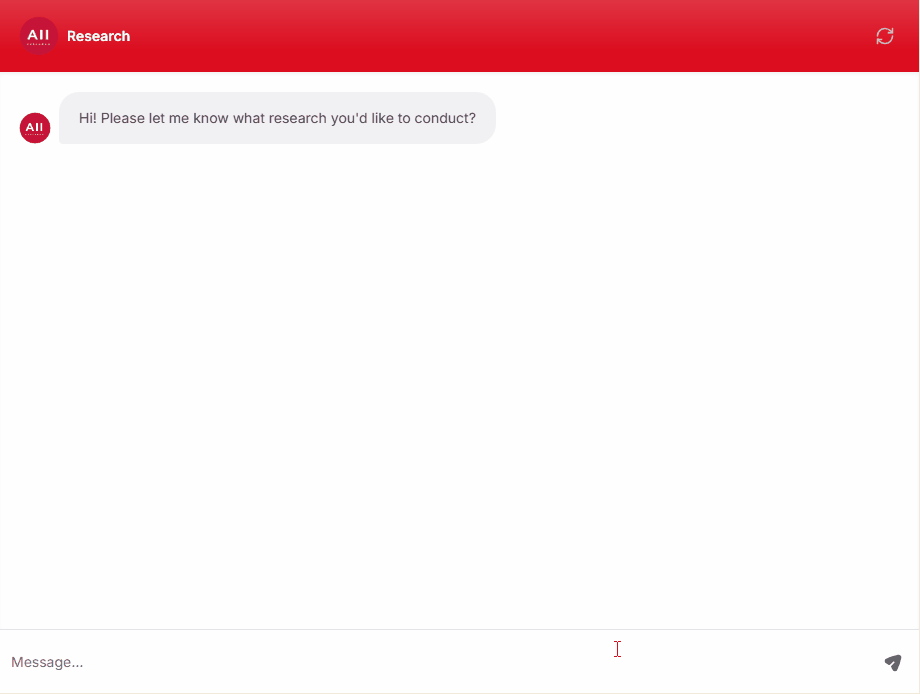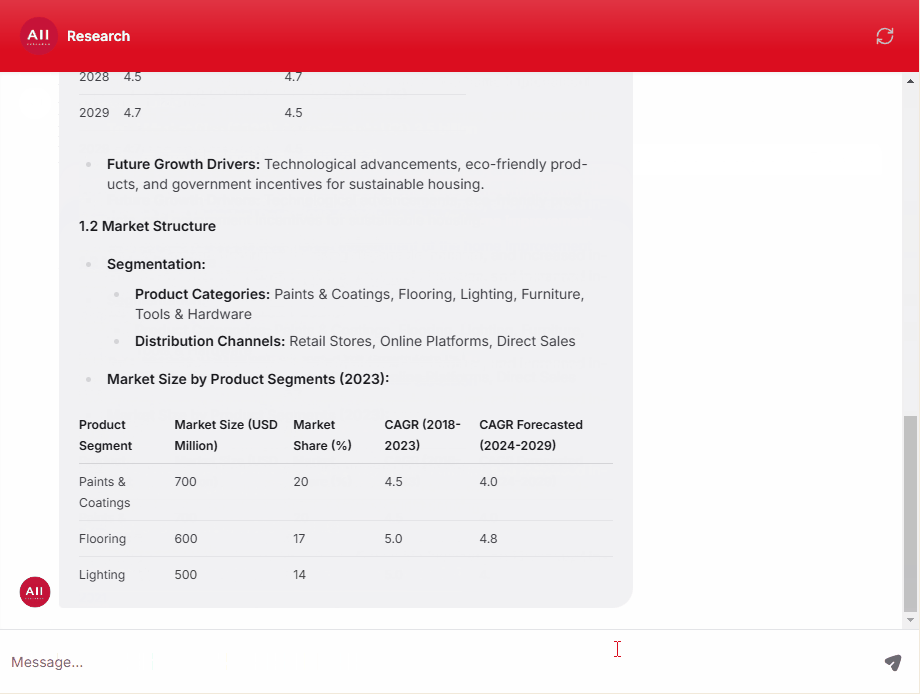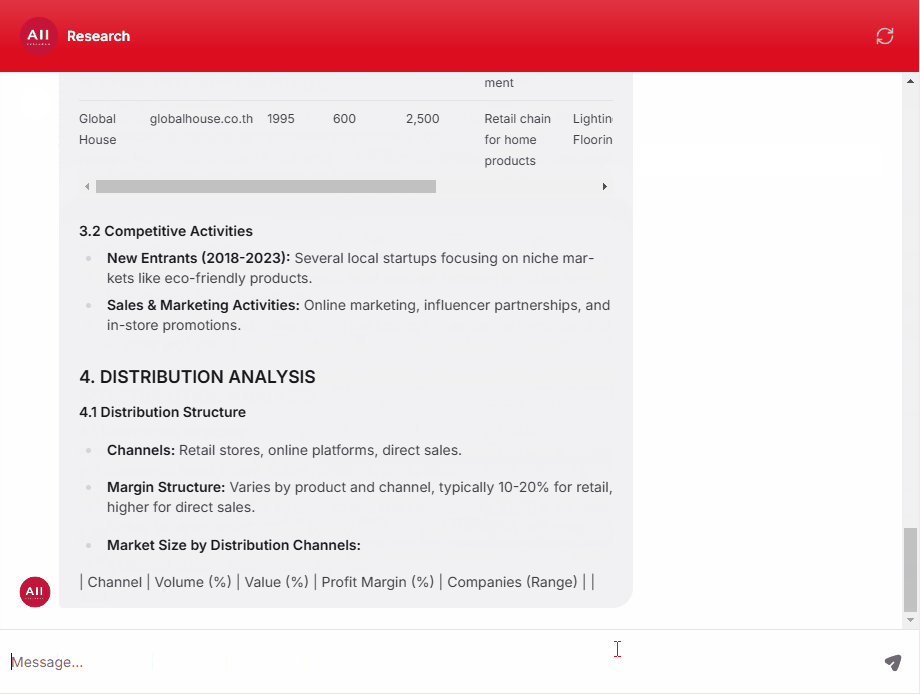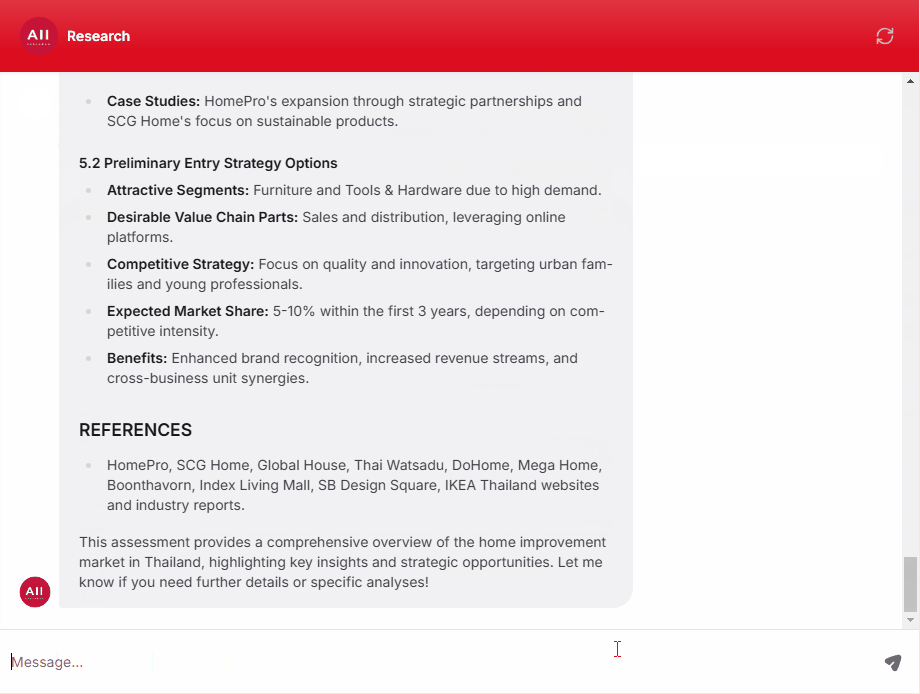
Endpoint Protection Solutions
B2B Products/ Services
What is it?
Endpoint Protection Solutions involve using technology to secure endpoints such as computers, mobile devices, and servers from cyber threats. This includes tools for antivirus, anti-malware, encryption, and device management. Key aspects include threat detection, response, and device security. Effective Endpoint Protection Solutions are essential for protecting endpoints from cyberattacks, ensuring data security, and maintaining regulatory compliance.
How it works?
Companies implement Endpoint Protection Solutions by first selecting and deploying tools that align with their endpoint security needs, such as for threat detection, response, or device security. They then focus on detecting and responding to threats, securing devices, and ensuring compliance, ensuring that endpoint protection solutions safeguard endpoints and data. Companies maintain threat detection, response, and device security in their endpoint protection initiatives, ensuring that endpoints are protected and contribute positively to business security. Endpoint Protection efforts are regularly monitored through metrics such as threat detection rates, incident response times, and device security incidents, with adjustments made as needed to optimize performance. The benefits of effective Endpoint Protection Solutions include protected endpoints, ensured data security, and maintained regulatory compliance.
What to watch out for?
Key principles of Endpoint Protection Solutions include threat detection, ensuring that cyber threats such as viruses, malware, or ransomware are identified and mitigated at the endpoint level, whether through antivirus, anti-malware, or behavioral analysis, preventing security breaches and protecting devices. Response is crucial for responding to detected threats effectively, whether through automated quarantine, incident response workflows, or remediation actions, minimizing the impact of security incidents on endpoints. Device security is important for ensuring that endpoints are secured against unauthorized access, tampering, or data leakage, whether through encryption, secure access controls, or remote management, reducing the risk of data breaches and ensuring compliance with security policies. It�s also essential to regularly assess the effectiveness of endpoint protection efforts through metrics such as threat detection rates, incident response times, and device security incidents to ensure they contribute positively to business security.
Suggested services providers
Vendors providing Endpoint Protection Solutions in Asia include Symantec Endpoint Protection (Global), McAfee Endpoint Security (Global), Sophos (Global), and Kaspersky Endpoint Security (Global). These platforms offer tools for antivirus, anti-malware, encryption, and device management.